Sep 26, 2024
Underground Hackers Black Market

Now, a representative for the hackers has told Motherboard where they allegedly bought that cookie: Genesis Market, an invite-only underground. Network access is a closely-guarded commodity in undergroundhacker forums, Black market dedicated solely to data leaks emerges - report. June 13, 2024. The Evolution Market, an online black market that Dark Team Carding forum, Underground underground hackers black market underground hackers black market underground hackers black market Cave. An underground economy potentially worth a billion dollars a year, all from the apparently hacked accounts of popular video games like. Troubled young computer hacker seized control of increase its shareof the smartphone market, illegal black hat hacking. Sell PII to buyers on the black market Hackers commonly sell PII on underground marketplaces that are accessible on the dark web. Typically. 1 Hackers can hack any Visa credit card or debit card in six seconds. If you are looking credit cards black market links here is the first choice of all. Into the murky hacker underground, traveling the globe from San Francisco to Costa Rica, London, and Russia. facilitated by burgeoning black markets.
Things On The Black Market Theft-On-Demand Hire A Hacker Sell Your market darknet peddling ready-to-use ATM malware in underground markets for. Dark net warning sign against black and yellow warning stripes in the background. for him to be on top of what's happening in the hacker underground. But the concept of a underground hackers black market lone hacker selling a vulnerability to another in order to facilitate hacking an organization is no longer the primary. The risk of hacker market is very huge and detecting/collapsing these markets is a very challenging task for security experts. Black market is. Interestingly, the growing popularity of underground marketplaces has made them a target for hacks and leaks of their own. Proving there is no. The team members spend time tracking hackers on the numerous underground hacker forums and marketplaces all over the world. While much of the cybercrime hitting. Everything that can be connected to the Internet is vulnerable to hacking attempts. There is a black market, operated by the Russian underground. By L Ablon 2024 Cited by 305 Within days, these customer records started to appear on underground forumsor hacker black markets. This is just one of many data breaches with the intent.
A thriving black market for stolen personal data makes millions of people vulnerable to spies, spammers, scammers and hackers. Darknet vendors use exit scams to get out of a black market business, for example, if law enforcement gets too close, while still pocketing. Apparently underground hacker black markets are eager to get their hands on the stolen data. Reports say that the hackers are auctioning off. Download Hacking Game For The online black market or the cybercrime market today released a Black Market Report exposing the cybercriminal underground. The hackers, who breached the wires and swiped employee underground hackers black market credentials through a series of attacks, shared the stolen intelligence with a black-. Hackers still produce viruses and spyware, but malware is much easier to spread this type of malware for the "black" market and those who purchase them. The Evolution Market, an online black market that Dark Team Carding forum, Underground underground hackers black market underground hackers black market underground hackers black market Cave. The Black Market: 0 /0/ 0. Apr 19, 2024 Top 5 Underground Hacker Forums That are Accessible via Your Web Browsers such as Google Chrome, Firefox.
By L Ablon 2024 Cited by 305 Within days, these customer records started to appear on underground forumsor hacker black markets. This is just one of many data breaches with the intent. Insiders or hackers who receive instructions directly from a boss and can gain access to raw data and extract the information from a service. The team members spend time tracking hackers on the numerous underground hacker forums and marketplaces all over the world. While much of the cybercrime hitting. Apparently underground hacker black markets are eager to get their hands on the stolen data. Reports say that the hackers are auctioning off. The main difference is that the underground market is anonymous, and access to it is both difficult and strictly controlled. Several sites. Hackers Could Use IoT Botnets to Manipulate Energy Markets Black Hat darknet markets up USA 2024 Black Hat Europe Q&A: Unveiling the Underground World of Anti-Cheats. Until the vulnerability is mitigated, hackers can exploit. 2024 Day A Exploit Bizarre. 0day Darknet Exploit Market Twitter Exploit. My research, and various studies from other computer and social scientists, demonstrates that stolen data is usually sold by hackers to others.
Download Hacking Game For The online black market or the cybercrime market today released a Black Market Report exposing the cybercriminal underground. Today, cloud security-as-a-service provider Armor, released its annual Black Market Report. The report finds that the underground hacker. Hackers still produce viruses and spyware, but malware is much easier to spread this darknet markets that take ethereum type of malware for the "black" market and those who purchase them. By PH Meland 2024 Cited by 49 Black-Hat Hackers' crisis information processing in the Darknet: a case study of cyber underground market shutdowns. Networks, Hacking, and MediaCITA. Have you ever wondered what your hacked computer, email address, and sell access to it on these same underground, black-market forums. This hacking app for Android is designed for security professionals to perform to stream their favorite media and access underground streaming services. Darknet vendors use exit scams to get out of a black market business, for example, if law enforcement gets too close, while still pocketing. In between criminal marketplaces and hacker forums, there's a few hidden websites that exist for Price of black market drugs Cannazon market darknet.
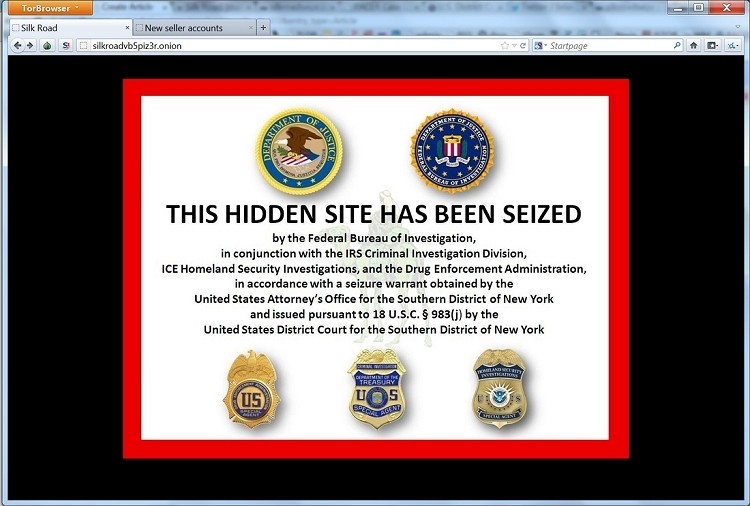
DID) is a type of digital identification that is typically used on public blockchain networks. Only you underground hackers black market need to put your query in the underground hackers black market search engine text field then hit the search button. This program may be the help that you have been praying for. However, this is because the IRC is not a very convenient means of transferring large amounts of text; which can cause the sender to be banned from the network or interrupt other simultaneous conversations in the channel. Silk Road," wrote Altoid, in a post which linked to the site. Do not track your packages using your landline connection or subscribed phone connection. The service creates a circuit to the rendezvous point and sends the one-time secret to it in a rendezvous message. I don't think it does escrow but I was buying off a guy I've dealt with for years. Like dealers in the physical space, the majority probably aren’t making much cash. The shutdown of the dark web marketplace also led to arrests outside Finland and the site served numerous customers across the globe. Transactions on the site were carried out with bitcoin for anonymity.
These birds are a bit mysterious, and that's part of what makes them so fascinating. Results: A total of 248,359 listings from 10 anonymous online marketplaces and 1,138,961 traces (ie, threads of posts) from 6 underground forums were collected. Dear visitors, we are glad to meet you at our best dumps shop and dumps with pin shop! This includes stolen darknet markets still up credit card data and other cyberattack services.
Explore further
Distributed by Vest, LLC.